Don’t let hidden vulnerabilities hold your business back. Please fill out the form below as the first step towards our comprehensive Cybersecurity Risk Assessment that will help protect your organization’s data, set up your business for long-term success, and ensure peace of mind.


Your Cybersecurity Risk Assessment Starts Here
Solution Page
Does Your Business Need a Cybersecurity Risk Assessment?
Do You Know The Full Story Of Your IT Infrastructure?
You might not, but that’s okay! Liberty Technology offers in-depth Cybersecurity Risk Assessments for businesses of all sizes.
Do you know everything about your current information technology setup? Are you aware of your technology stack? Do you know what software you’re using? What software you’re paying for but not using? Do you know your data security vulnerabilities?
Odds are, you don’t know all of these answers, which means your business isn’t running at a level it could reach with a proper IT infrastructure. At Liberty Technology, we created our Cybersecurity Risk Assessment — sometimes referred to as a business risk assessment or CSRA — to help businesses identify existing weaknesses in operational maturity and information security, and how they can improve upon existing strengths. You’ll be able to answer all of the questions we just asked once our CSRA is completed.
Our risk assessments take around 2-4 weeks to complete and, at the end of the process you’ll receive a detailed report showing where you need to improve, what our recommendations are to make those improvements, and what an appropriate IT budget would look like. You can take this information to another IT firm, or we can partner together to implement our plan… it’s entirely up to you.
At Liberty Technology, our goal is to scale IT for what your business needs now, what it needs in the near term, and what it needs looking toward the future. We’re here to help your business achieve operational maturity and run as efficiently as possible, letting you focus on what you do best.
Testimonials
Our Services

Physical Security
Physical Security
At Liberty Technology, we are your source for physical security services that are designed to give businesses the protection they need in Griffin, GA and beyond. Our physical security services can keep your business assets and people protected from intrusion and harm no matter your industry, including manufacturing, retail, government, education, property management, hospitality, healthcare, and others. We offer the business alarm systems, access control systems, and surveillance technology you need for your facility.

Secure
Secure
The best defense against today’s advanced security threats is a good offense – one that outsmarts emerging threats while they’re still just threats. Ineffective firewalls, unmanaged email, and unprotected devices are behind the vast majority of security breaches. To stay ahead of these dangers, you need to know who is on your network, what they’re doing there, and how to respond quickly when something’s not right. A total security solution protects your networks, data, and devices in today’s mobile environment, keeping your enterprise safe, compliant, and agile as it grows.

Collab
Collab
Finding a time and place to suit team members on the move can seem nearly impossible. Plus, trying to coordinate across a multitude of communications choices can lead to lost invites, delayed responses, and missed meetings or deadlines. The right collaboration technology simply must agree with what teamwork looks like today.
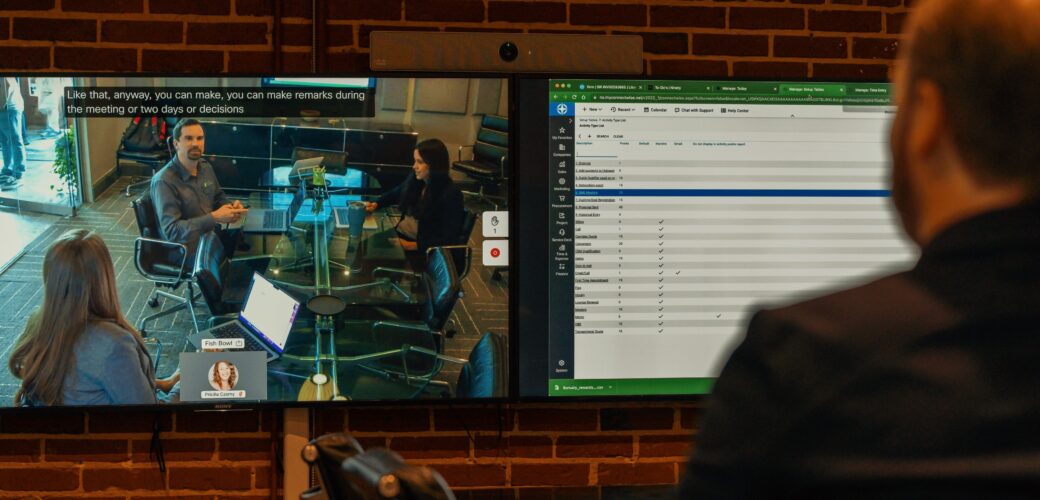
Webex
Webex
Work isn’t where you are but what you do. Webex provides the most intuitive collaboration software on the market, allowing you to work from anywhere in the world with an Internet connection.

Endpoints
Endpoints
Having the right endpoints can boost an employee’s productivity while keeping support costs down. We can help you source the exact endpoints to ensure the entire team runs at peak efficiency.

Connect
Connect
Our Connect solutions include everything from running fiber optic cabling to implementing a city-wide WiFi network. Employees and guests enjoy fast and secure wireless access and can switch access points seamlessly with unbroken coverage. Enforce device security policies, deploy software and apps, and perform remote, live troubleshooting on thousands of managed devices.

Office Network
Office Network
Liberty Technology understands how modern businesses and offices need to work. Being able to plug in from anywhere in the world or in the main office, having a secure, fast, and effective network adds efficiency to your business. No matter how you work, we’re here to help your business grow.

Compute
Compute
From endpoints to servers, switching to storage, and all the way up to datacenter and hyperconverged solutions, if it connects to the network we’ve got it covered. We’ll work with you to identify what you need (and what you don’t), plan for the future, and make sure you’ve got all the right tools in all the right places.

Virtual CIO
Virtual CIO
As a Virtual CIO, our team evaluates the responsibilities of what is needed of an IT Manager based on your company’s specific needs and develops an IT Roadmap and Budgeting Guide. This includes the design of a road map, a high-level concept, that will act as a guide in improving your technology as it deems fit in order to keep productivity of your business top priority.

Managed IT
Managed IT
As a Managed Service Provider, we at Liberty Technology provide services, support, and solutions in the four core areas of Collab, Compute, Connect, and Secure. We call these our four pillars. These are our areas of expertise. Our proven approach to how we design, transition, and manage these solutions is what sets us apart.
Physical Security


At Liberty Technology, we are your source for physical security services that are designed to give businesses the protection they need in Griffin, GA and beyond. Our physical security services can keep your business assets and people protected from intrusion and harm no matter your industry, including manufacturing, retail, government, education, property management, hospitality, healthcare, and others. We offer the business alarm systems, access control systems, and surveillance technology you need for your facility.
Secure

The best defense against today’s advanced security threats is a good offense – one that outsmarts emerging threats while they’re still just threats. Ineffective firewalls, unmanaged email, and unprotected devices are behind the vast majority of security breaches. To stay ahead of these dangers, you need to know who is on your network, what they’re doing there, and how to respond quickly when something’s not right. A total security solution protects your networks, data, and devices in today’s mobile environment, keeping your enterprise safe, compliant, and agile as it grows.
Collab

Finding a time and place to suit team members on the move can seem nearly impossible. Plus, trying to coordinate across a multitude of communications choices can lead to lost invites, delayed responses, and missed meetings or deadlines. The right collaboration technology simply must agree with what teamwork looks like today.
Webex


Work isn’t where you are but what you do. Webex provides the most intuitive collaboration software on the market, allowing you to work from anywhere in the world with an Internet connection.
Endpoints


Having the right endpoints can boost an employee’s productivity while keeping support costs down. We can help you source the exact endpoints to ensure the entire team runs at peak efficiency.
Connect


Our Connect solutions include everything from running fiber optic cabling to implementing a city-wide WiFi network. Employees and guests enjoy fast and secure wireless access and can switch access points seamlessly with unbroken coverage. Enforce device security policies, deploy software and apps, and perform remote, live troubleshooting on thousands of managed devices.
Office Network


Liberty Technology understands how modern businesses and offices need to work. Being able to plug in from anywhere in the world or in the main office, having a secure, fast, and effective network adds efficiency to your business. No matter how you work, we’re here to help your business grow.
Compute


From endpoints to servers, switching to storage, and all the way up to datacenter and hyperconverged solutions, if it connects to the network we’ve got it covered. We’ll work with you to identify what you need (and what you don’t), plan for the future, and make sure you’ve got all the right tools in all the right places.
Virtual CIO


As a Virtual CIO, our team evaluates the responsibilities of what is needed of an IT Manager based on your company’s specific needs and develops an IT Roadmap and Budgeting Guide. This includes the design of a road map, a high-level concept, that will act as a guide in improving your technology as it deems fit in order to keep productivity of your business top priority.
Managed IT

As a Managed Service Provider, we at Liberty Technology provide services, support, and solutions in the four core areas of Collab, Compute, Connect, and Secure. We call these our four pillars. These are our areas of expertise. Our proven approach to how we design, transition, and manage these solutions is what sets us apart.



